Earlier this week on Monday, Microsoft launched Project Freta, a new free virtual machine (VM) forensics service that will help users detect malware in memory on cloud infrastructure.
Project Freta is different from Microsoft’s commercial security solution like Microsoft Defender ATP as it comes from Microsoft Research and is currently classified as a ‘technology demonstration’.
This new cloud service can detect rootkits and sophisticated malware by analyzing memory snapshots of live Linux system. Even though Snapshot-based memory forensics is a pretty old security method, but no major cloud provider had made it available for users until now.
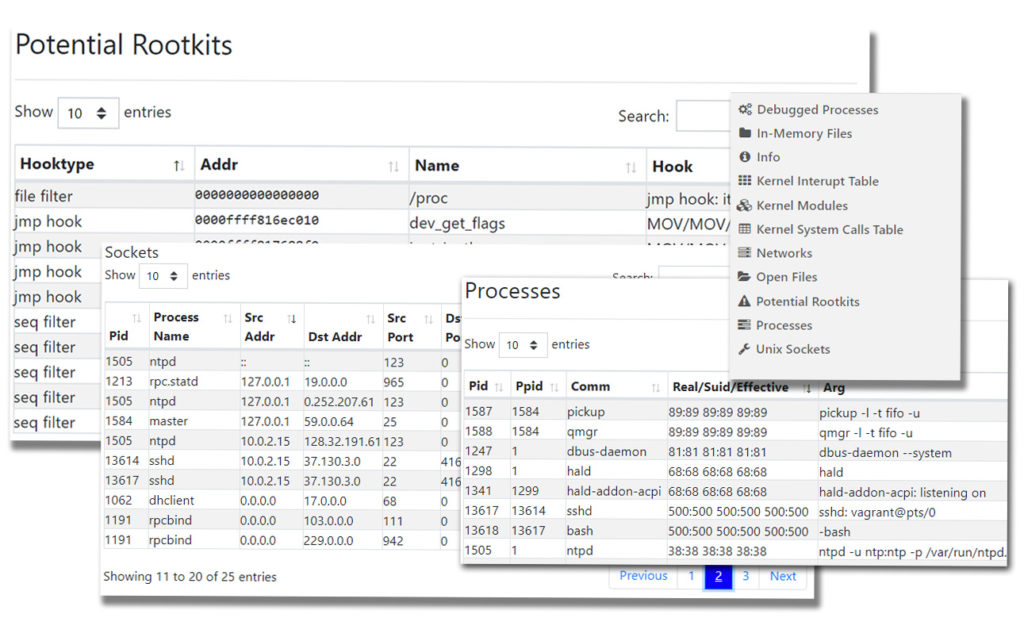
For that, it will analyze processes, global values and addresses, kernel components, networks, in-memory files, debugged processes, ARP tables, open files, open sockets, and Unix sockets.
By using Project Freta, customers will be able to conduct full memory audits of thousands of cloud-based Linux VMs in an automated manner. It will help every user and enterprise to scan volatile memory for malware just at the click of a button with no setup required.
The service uses sensors designed to detect malware without alerting the malicious software. Microsoft’s idea behind this technique is that the malware cannot detect the sensor before installing itself, neither it can hide somewhere it would not be seen by the sensor. So the malware cannot detect the sensor and remove or change itself, or modify the sensor to avoid detection.
Also Read: Microsoft Launches App To ‘Recover Deleted Files’ In Windows 10
Microsoft’s Project Freta is currently available for free with no limit on usage. It is available as a portal where you can upload images of your OS for analysis and the results can be accessed directly on the portal or through REST and Python APIs. Right now, the service supports over 4,000 kernel versions.
The post Microsoft’s Project Freta: A New Free Service To Spot Malware In Cloud VMs appeared first on Fossbytes.
Microsoft’s Project Freta: A New Free Service To Spot Malware In Cloud VMs
read more
No comments:
Post a Comment